In this last blog, we learn about
what is cryptography?
what is the use of cryptography?
Implementation of the practice of client and server interacting with each other and also the use of another password if the hacker is present in the middle of the network.
Uses cases of the WireShark and how to use it.
In this blog, we are going to see some of the advanced concepts of Cryptography.
What is PKI and What is it used for?
The Public key infrastructure (PKI) is the set of hardware, software, policies, processes, and procedures required to create, manage, distribute, use, store, and revoke digital certificates and public keys. PKIs are the foundation that enables the use of technologies, such as digital signatures and encryption, across large user populations. PKIs deliver the elements essential for a secure and trusted business environment for e-commerce and the growing Internet of Things (IoT).
PKIs help establish the identity of people, devices, and services – enabling controlled access to systems and resources, protection of data, and accountability in transactions. Next-generation business applications are becoming more reliant on PKI technology to guarantee high assurance because evolving business models are becoming more dependent on electronic interaction requiring online authentication and compliance with stricter data security regulations.
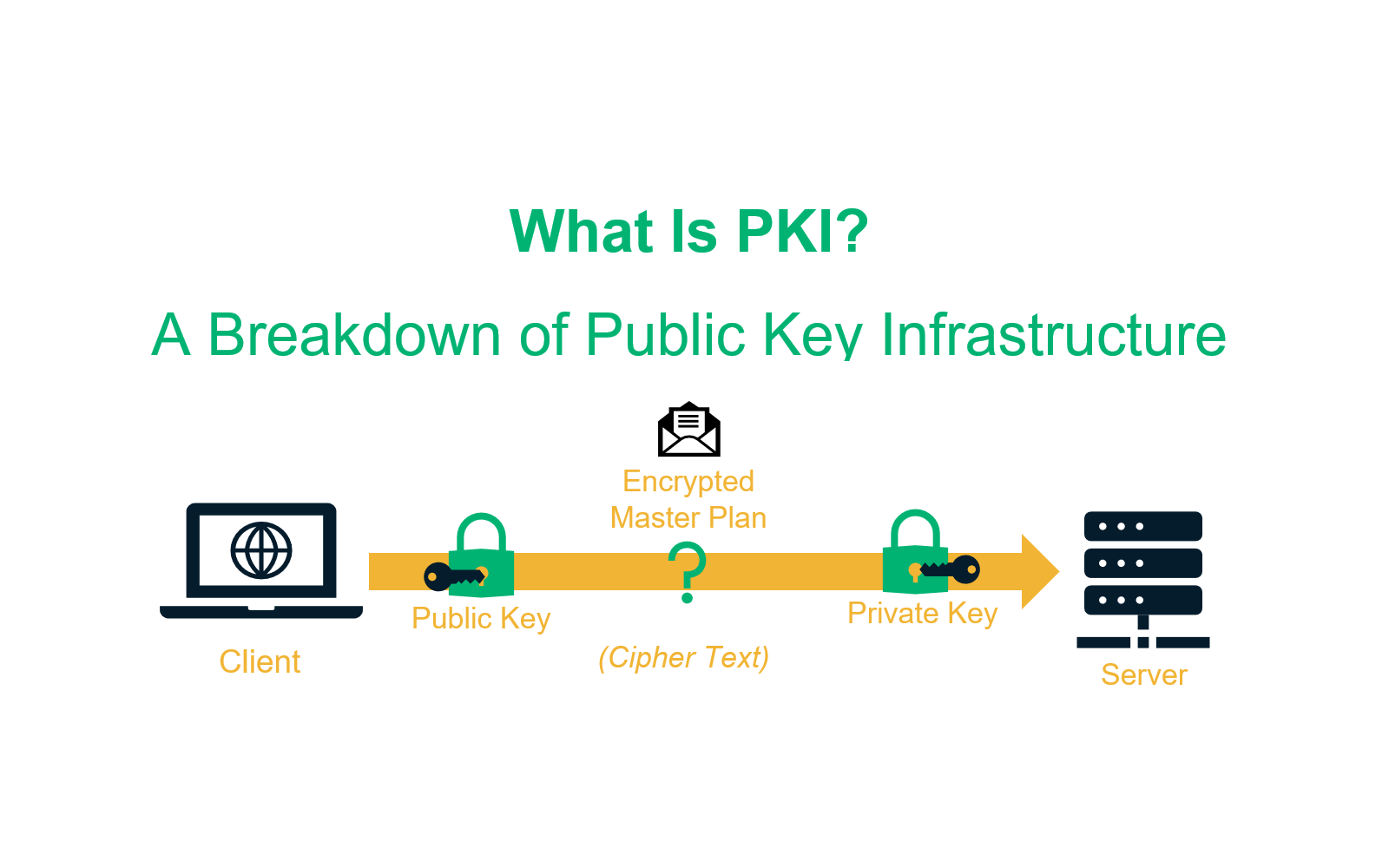
Working on a PKI:
Let us understand the working of PKI in steps.
PKI and Encryption: The root of PKI involves the use of cryptography and encryption techniques. Both symmetric and asymmetric encryption uses a public key. The challenge here is – “How do you know that the public key belongs to the right person or to the person you think it belongs to?”. There is always a risk of MITM(Man in the middle). This issue is resolved by a PKI using digital certificates. It gives identities to keys in order to make the verification of owners easy and accurate.
Public Key Certificate or Digital Certificate: Digital certificates are issued to people and electronic systems to uniquely identify them in the digital world. Here are a few noteworthy things about a digital certificate. Digital certificates are also called X.509 certificates. This is because they are based on the ITU standard X.509.
The Certification Authority (CA) stores the public key of a user along with other information about the client in the digital certificate. The information is signed and a digital signature is also included in the certificate.
The affirmation for the public key then thus be retrieved by validating the signature using the public key of the Certification Authority.
Certifying Authorities: A CA issues and verifies certificates. This authority makes sure that the information in a certificate is real and correct and it also digitally signs the certificate. A CA or Certifying Authority performs these basic roles:
Generates the key pairs – This key pair generated by the CA can be either independent or in collaboration with the client.
Issuing of the digital certificates – When the client successfully provides the right details about his identity, the CA issues a certificate to the client. Then CA further signs this certificate digitally so that no changes can be made to the information.
Publishing of certificates – The CA publishes the certificates so that the users can find them. They can do this by either publishing them in an electronic telephone directory or by sending them out to other people.
Verification of certificate – CA gives a public key that helps in verifying if the access attempt is authorized or not.
Revocation – In case of suspicious behavior of a client or loss of trust in them, the CA has the power to revoke the digital certificate.
AES algorithm
Advanced Encryption Standard (AES) is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001. AES is widely used today as it is a much stronger than DES and triple DES despite being harder to implement.
Points to remember
AES is a block cipher.
The key size can be 128/192/256 bits.
Encrypts data in blocks of 128 bits each.
Step to follow for the Encryption of the AES algorithm
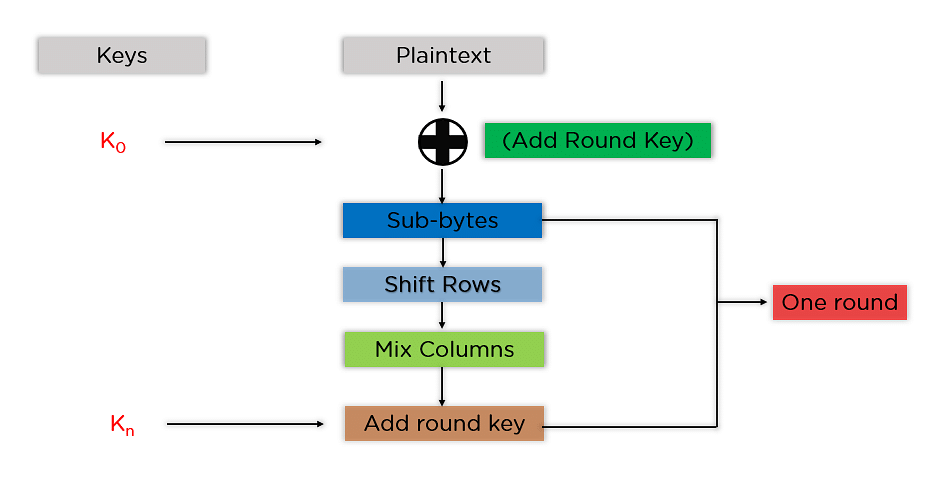
Derive the set of round keys from the cipher key.
Initialize the state array with the block data (plaintext).
Add the initial round key to the starting state array.
Perform nine rounds of state manipulation.
Perform the tenth and final round of state manipulation.
Copy the final state array out as the encrypted data (ciphertext).
What Are the Applications of AES?
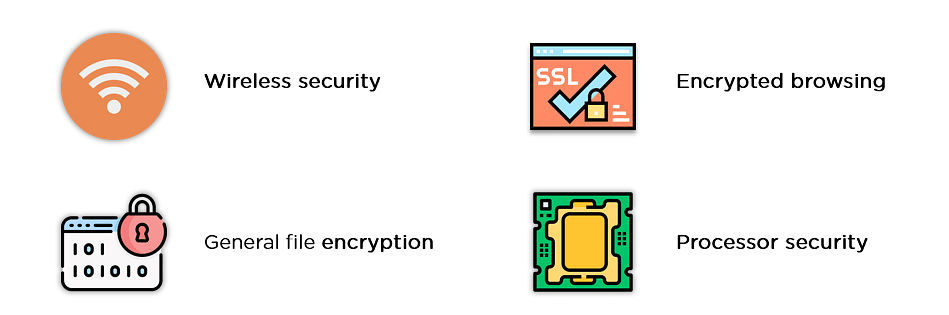
The applications of the AES Encryption algorithm are as follows:
- Wireless Security: Wireless networks are secured using the Advanced Encryption Standard to authenticate routers and clients. WiFi networks have firmware software and complete security systems based on this algorithm and are now in everyday use.
Encrypted Browsing: AES plays a huge role in securing website server authentication from both the client and server end. With both symmetric and asymmetric encryption being used, this algorithm helps SSL/TLS encryption protocols to always browse with the utmost security and privacy.
General File Encryption: Apart from corporate necessities, AES is also used to transfer files between associates in an encrypted format. The encrypted information can extend to chat messages, family pictures, legal documents, etc.
Processor Security: Many processor manufacturers enable hardware-level encryption using the likes of AES encryption to bolster security and prevent meltdown failures, among other low-profile risks.
SSL/TLS Handshake
What is Handshake?
An SSL/TLS handshake is a negotiation between two parties on a network – such as a browser and a web server – to establish the details of their connection. It determines what version of SSL/TLS will be used in the session, which cipher suite will encrypt communication, verifies the server (and sometimes also the client), and establishes that a secure connection is in place before transferring data.
This all happens in the background, thankfully – every time you direct your browser to a secure site a complex interaction takes place to make sure that your data is safe.
How SSL handshake connection is established.
The client sends a request to the server for a secure session. The server responds by sending its X.509 digital certificate to the client.
The client receives the server's X.509 digital certificate.
The client authenticates the server, using a list of known certificate authorities.
The client generates a random symmetric key and encrypts it using the server's public key.
The client and server now both know the symmetric key and can use the SSL encryption process to encrypt and decrypt the information contained in the client request and the server response.
What is the SHA-256 Algorithm?
SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family, which was slowly losing strength against brute force attacks.
The significance of the 256 in the name stands for the final hash digest value, i.e. irrespective of the size of plaintext/cleartext, the hash value will always be 256 bits.
The other algorithms in the SHA family are more or less similar to SHA 256. Now, look into knowing a little more about their guidelines.
What are the Characteristics of the SHA-256 Algorithm?
Some of the standout features of the SHA algorithm are as follows:
Message Length: The length of the cleartext should be less than 264 bits. The size needs to be in the comparison area to keep the digest as random as possible.
Digest Length: The length of the hash digest should be 256 bits in SHA 256 algorithm, 512 bits in SHA-512, and so on. Bigger digests usually suggest significantly more calculations at the cost of speed and space.
Irreversible: By design, all hash functions such as the SHA 256 are irreversible. You should neither get a plaintext when you have the digest beforehand nor should the digest provide its original value when you pass it through the hash function again.
Now that you got a fair idea about the technical requirements for SHA, you can get into its complete procedure, in the next section.
Steps in SHA-256 Algorithm
SHA-256 is a cryptographic hash function that takes an input message of any length and produces a fixed-size output of 256 bits. The following are the basic steps of the SHA-256 algorithm:
Padding: Append the bit "1" to the end of the message, followed by enough "0" bits to make the message length congruent to 448 mod 512. Then append the length of the original message as a 64-bit big-endian integer.
Initialization: Initialize the hash values, which are eight 32-bit words denoted by H0 through H7, to specific constants.
Message Schedule: Break the padded message into 512-bit blocks and expand each block into a 64-word message schedule using a fixed formula.
Compression: Iterate over each block of the message schedule and update the hash values using a compression function that mixes the values of the message schedule with the current hash values.
Output: The final hash value is the concatenation of the eight 32-bit hash values in the order H0 through H7.
These steps are repeated for each input message, and the resulting hash value is typically used to verify the integrity and authenticity of the message.
In the next blog, we are going to see about the
Secure connection using httpd
Self-sign concept of Secure Web connection.
Implementation of all the concept
That's all for this blog and stay tuned for more Cryptography tutorials and more such tech. Make sure to subscribe to our newsletter.
Thank you for Reading:)
#Happy Reading!!
Any query and suggestion are always welcome - Nehal Ingole