Introduction to Cryptography
Understanding secure communication in the presence of malicious third-parties
Cryptography is the technique of securing information and communications through the use of codes so that only those persons for whom the information is intended can understand and process it. In Cryptography the techniques which are used to protect information are obtained from mathematical concepts and a set of rule-based calculations known as algorithms to convert messages in ways that make it hard to decode them. These algorithms are used for cryptographic key generation, digital signing, verification to protect data privacy, web browsing on the internet, and protecting confidential transactions such as credit card and debit card transactions.
Techniques used For Cryptography: In today’s age of computers cryptography is often associated with the process where an ordinary plain text is converted to cipher text which is the text made such that the intended receiver of the text can only decode it hence this process is known as encryption. The process of conversion of cipher text to plain text is known as decryption.
History of Cryptography
Cryptography in the Computer Age
With the rise of computers, cryptography became vastly more advanced than it was in the analog era. 128-bit mathematical encryption, far stronger than any ancient or medieval cipher, is now the standard for many sensitive devices and computer systems. Beginning in 1990, an entirely new form of cryptography, dubbed quantum cryptography, was under development by computer scientists hoping to once again elevate the level of protection offered by modern encryption.
More recently, cryptographic techniques have also been used to make cryptocurrencies possible. Cryptocurrencies leverage several advanced cryptographic techniques, including hash functions, public-key cryptography, and digital signatures. These techniques are used primarily to ensure the security of data stored on blockchains and to authenticate transactions. A specialized form of cryptography, known as an Elliptical Curve Digital Signature Algorithm (ECDSA), underpins Bitcoin and other cryptocurrency systems as a means of providing extra security and ensuring that funds can only be used by their rightful owners.
Cryptography has come a long way in the last 4,000 years, and it isn’t likely to stop anytime soon. As long as sensitive data requires protection, cryptography will continue to advance. Although the cryptographic systems used in cryptocurrency blockchains today represent some of the most advanced forms of this science, they are also part of a tradition that extends back through much of human history.
What is the need for Cryptography?
In the security environment, integrity refers to the fact that information systems and their data are accurate. If a system possesses integrity, it means that the data in the system is moved and processed in predictable ways. Even when the data is processed, it doesn’t change.
Cryptography ensures the integrity of data using hashing algorithms and message digests. By providing codes and digital keys to ensure that what is received is genuine and from the intended sender, the receiver is assured that the data received has not been tampered with during transmission.
Client and Server interacting with each other
Let's do the practical demo for understanding the need for Cryptography in computer
At the first create a website and launch it. Website work on the HTTP protocol which is not a secure protocol. It will convert the data into a packet and the packet is sent to the server in clear text (anyone can read the text if they open the packet). The connection packet is sent by the client to the server but there is one big problem came to the packet is going packet anyone or service provider can easily see our packet and capture the client's important data and sell it to the hacker or in the dark web.
Requirement :
AWS EC2-Instance or Local Machine
WireShark Software
Command Prompt or Putty
In this practical, we are going to so how actually the packet is sent from client to server.
At the first launch of an EC2-instance
What is EC2 and how it works?
Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides secure, resizable computing capacity in the cloud. It is designed to make web-scale cloud computing easier for developers.
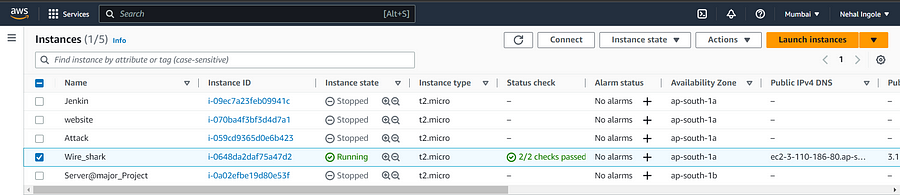
You can see the instance launch successfully, we can configure our httpd server in it. For that just copy the Public IP address of Ec2-instance and use the command prompt or putty to launch the instance.
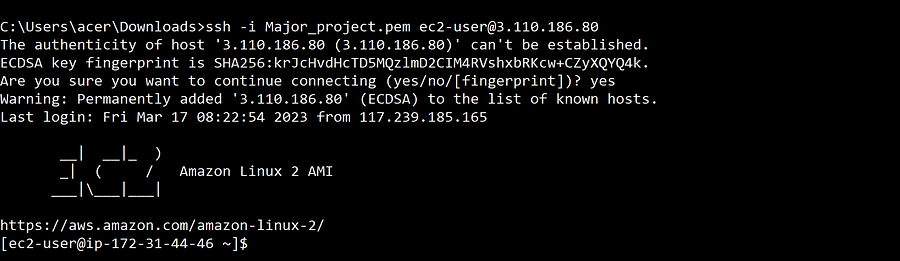
If you are using the command prompt just locate the private_key of the instance and open that particular location or folder in the command prompt by using ssh connect them.
ssh -i Private_key ec2-user@Public_IP
For launching a website, we need to install httpd server in our instance by using
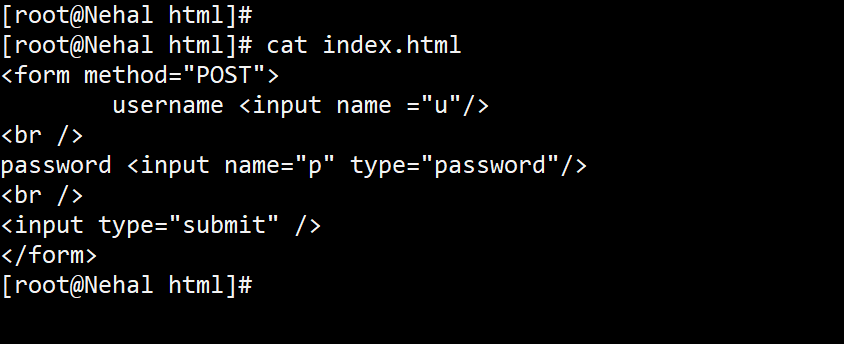
After the installation configure the webpage in /var/www/html by creating a file with the extension “ .html ”
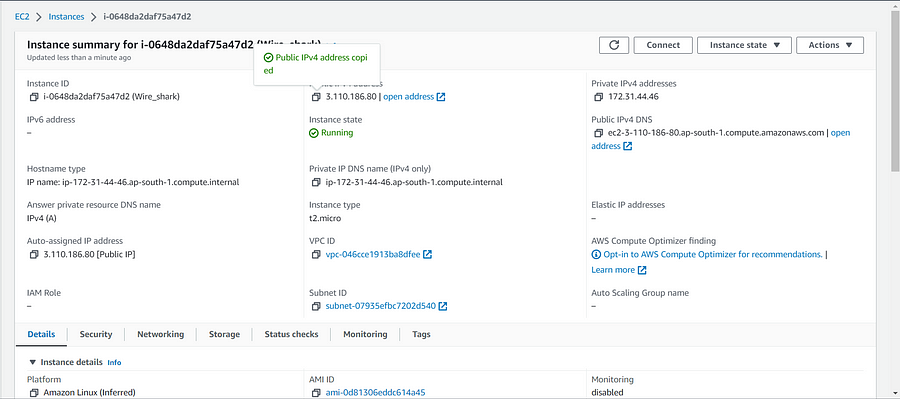
Copy the public address and paste it into the browser
After hitting the browser you can see the webpage enter your username and password (on this website we are not using any database to store our data, so data is not going stored anywhere)
Open Wireshark and start capturing the packet
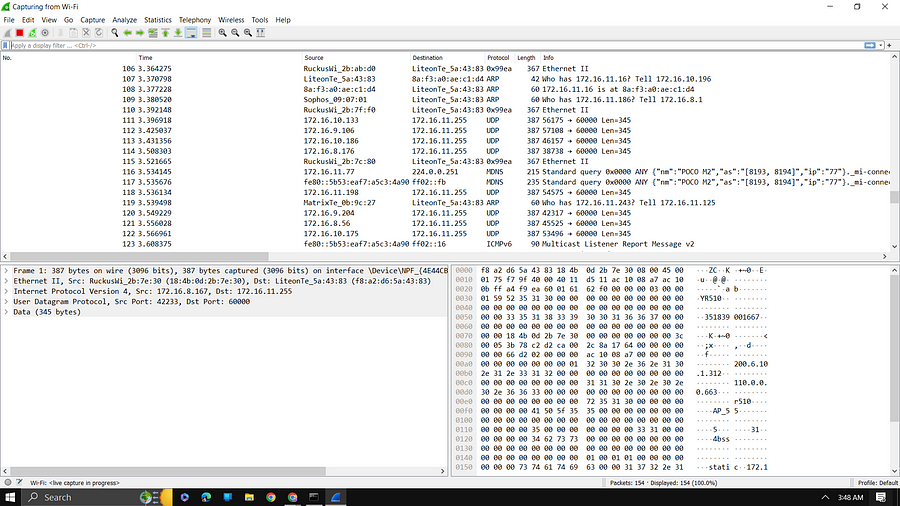
A laptop is connected to WiFi and the website is also hit by using the Same WiFi
For sorting the packet just use ip.addr==”Public_IP”
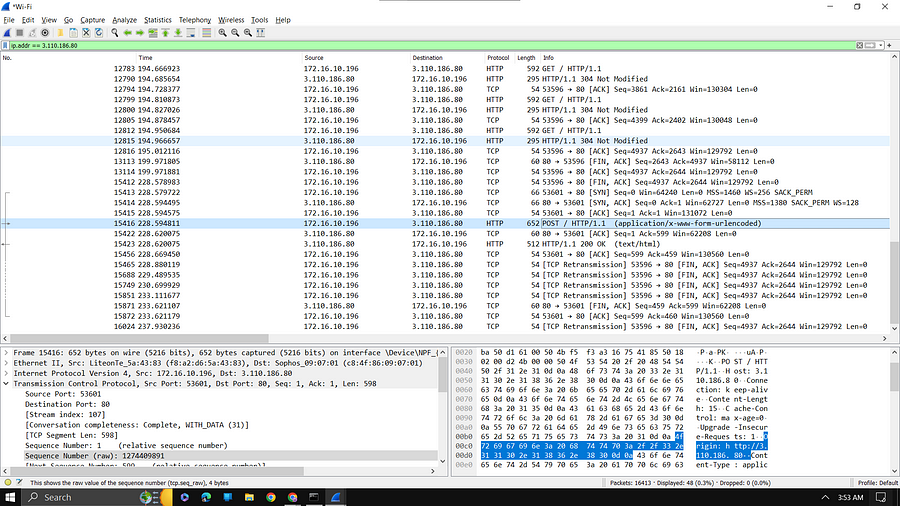
You can see HTTP (Selected portion) packet, Wireshark has traced that packet, and your service provider or any can see the Username and password of the client.

By using the packet anyone can see our username and password. In most cases, the username and password are seen by the service provider company.
By using the cryptographic we can secure our data by encryption technique
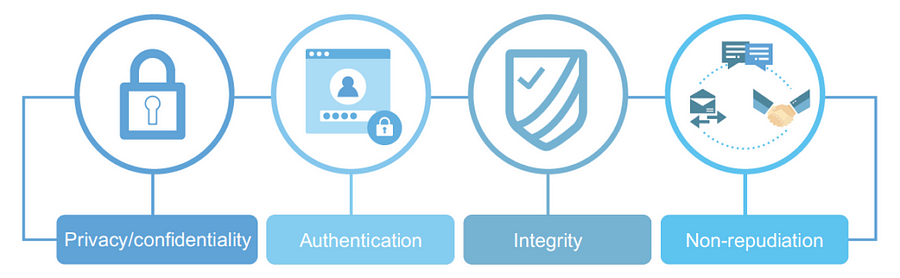
Confidentiality: Information can only be accessed by the person for whom it is intended and no other person except him can access it.
Integrity: Information cannot be modified in storage or transition between sender and intended receiver without any addition to information being detected.
Non-repudiation: The creator/sender of information cannot deny his intention to send information at a later stage.
Authentication: The identities of the sender and receiver are confirmed. As well as destination/origin of the information is confirmed.
The company that uses cryptography
Cosmian: Cosmian is a decentralized data intelligence platform that uses advances in functional and homomorphic encryption, it allows queries and calculations to be performed on encrypted private data without revealing the data itself.
Safeheron: Safeheron is an open-source one-stop self-custody solution provider, founded by a team with more than a decade of experience in cybersecurity and cryptography. Based on self-developed MPC (Multi-Party Computation) and TEE (Trusted Execution Environment) technologies, and with flexible policy configuration for complex business needs, Safeheron enables institutions to gain access to trusted, transparent industry-leading institutional-grade security features.
Committed to transparency and openness, Safeheron will continue to be a self-custody digital asset infrastructure that all enterprises can afford in Web3.AuroraChain: The latest smart contract platform that would apply unique consensus mechanisms and blockchain feature to build a more secure and “speed of light” operation to link a variety of industries like games, IoT, big data, and AI. They aim to resolve smart contract issues such as congestion, scalability, and upgradability. Aurora Chain applies DPOS+BFT consensus mechanisms and contracts with a “speed of light” operation rate to link industries such as games, big data, AI, and IoT.
Application of Cryptography
Digital Currencies
Secure Web browsing
Digital Signature
Encryption
Authentication
That's all for this blog and stay tuned for more Cryptography tutorials and more such tech. Make sure to subscribe to our newsletter.
Thank you for Reading:)
#Happy Reading!!
Any query and suggestion are always welcome - Nehal Ingole
